Blockchain 101 for Blockheads — What even is Blockchain?
We have all heard of “blockchain”, a term being thrown around like it’s today’s holy grail or Willy Wonka’s golden ticket to the future.
Simply throw in the words “blockchain” or “cryptocurrency” into what you are discussing, and you will sound smart and way ahead of the curve. But what actually is blockchain? Do most people understand exactly what it is?
Yes, blockchain will undeniably be crucial in the future. But it is one thing to know about it, and another to know what it actually is and how it works.
What is Blockchain in the first place?
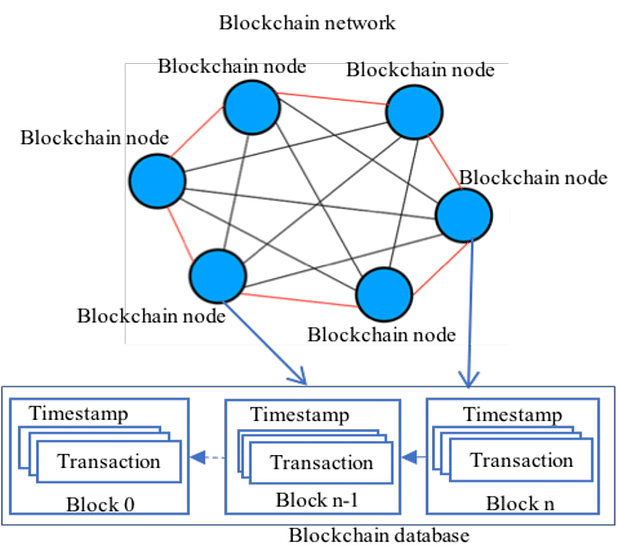
Fundamentally, blockchain is a type of database.
Database: a collection of structured information (data) which is stored electronically in a computer. This data or information stored can be easily accessed, managed, modified, and organized — usually, in very large amounts and by many users at any one time.
But how a blockchain stores data is a little different.
Instead of storing data in a conventional method e.g. spreadsheet or table format, a blockchain stores its data in blocks, which are linked or chained together (hence, a “blockchain” is essentially a chain of blocks).
New incoming data is filled into a new block. This newly-filled block is then chained onto the previous block of the existing blockchain. The process repeats as new data comes in. Thus, this makes the blocks of data linked together in chronological order and forming a timeline of data, because each block is provided an exact timestamp when it is first added to the blockchain.
Of course, since blockchain is a database, it needs computers (or “nodes”) to store the data. Each node or computer/device basically contains a full copy of the entire transaction history of the blockchain — so, you could say that a blockchain exists on its nodes.
For example, Bitcoin (a cryptocurrency) uses a blockchain network, which stores data of Bitcoin transactions — and the data is stored on the computers of the Bitcoin network’s users. However, due to the decentralized nature of the Bitcoin blockchain, these computers are not all under one roof. Instead, each computer (or group of computers) is with a different individual (or group of individuals). Such individuals are not limited by their geographical region — they could be at totally different ends of the world, but still part of the same network holding the blockchain.
Centralized blockchains also exist. They are private blockchains maintained by computers which are either under the same roof, or owned and operated by a single person, group, company or organization etc.
Source: IEEE Communications Surveys & Tutorials¹
How does Blockchain work then?
“How does data get recorded on the blockchain at all?” you may ask. Let’s attempt to break down the process.

Source: PWC²
Authentication of transaction
First, each user on the blockchain network has their own (1) private key (only users themselves can see) and (2) public key (which everyone can view). Using both of them creates a secure digital identity to authenticate the user and the transaction they wish to execute.
A key is a simply a piece of information which is used to encode or decode something. Similar to a physical key, it locks up data (encryption) such that only a person who has the right key can unlock the data (decryption).
Encryption/encoding: taking plain information and converting it into secret code, to protect the confidentiality of the message within. Essentially, encryption is to prevent non-intended people from reading text/data without a secret key. One of the most famous and simplest encryption techniques is the Caesar Cipher.
Blockchains use asymmetric encryption. This means that all users on the blockchain network has two keys — a private and public one. The public key is openly accessible to all users and is used to encrypt a message/data, while the private key is known only to an individual user and is used to decrypt an encoded message. This is like a mailbox — you can share your mailing address with everyone (public key), but you don’t share your mailbox key with others (private key). Thus, anyone can send you letters, but only you can read them.
So, for example for cryptocurrency like Bitcoin, anyone on the network can send you Bitcoins since anyone can see your public key (i.e. your wallet “address”), but only you can spend or transfer them out of your wallet because only you know your private key (it’s like your PIN/password).

Source: twilio³
Symmetric encryption: everyone on the same network uses just ONE key (for both encryption and decryption of the data). This means that everyone on the network can read all encoded messages. However, an outsider who steals the key from just one network member will be able to read everything as well. Hence, this is less secure than asymmetric encryption.
Put simply, you require the private key to “sign” off a transaction you wish to make. Thus, no one else can make a transaction on your behalf or forge this signature without your private key. Once the transaction is authenticated and agreed as between users, we proceed to the next step — validation.
Validation and Consensus
Once a transaction has been agreed between users, it needs to be validated before the new block containing the transaction is added to the blockchain via a “consensus” mechanism.
Validation is NOT consensus — the former comes before the latter. Validation is verifying that transactions are legitimate (i.e not fraudulent or amounting to double spending etc). Consensus is agreeing the ORDER of events/transactions on the blockchain. Thus, there could be a validated transaction which does is NOT agreed upon by the network (i.e. validated but fails consensus).
When a transaction is made, the whole blockchain network is notified. Some users of the network will attempt to validate that these transactions are “legitimate” — these people are called miners. Each miner will build his own block by including new transactions inside — and each miner’s block may be completely different from that of the other miners. After which, whether a particular miner’s block will be included in the blockchain’s record will be determined by a “consensus” decision — i.e. the majority (>50%) of nodes or computers in the network must agree that the transaction is valid.
- A miner may build a block consisting of completely legitimate transactions, but his block may still fail to be picked and achieve consensus by the network. He then has to create a new block and try again.
- For example, Amy and Bob are miners who each create their own blocks containing legitimate transactions. Amy creates a block consisting of Transactions A, B and C, whereas Bob creates a block consisting of Transaction C, D and E. Here, both blocks include the same Transaction C, e.g. that Carol pays Duncan 1 Bitcoin. If both Amy and Bob were to add their blocks in the blockchain, then the transaction will be duplicated — i.e. Carol now pays Duncan twice, paying Duncan 2 Bitcoin instead. Moreover, Carol may only have 1 Bitcoin initially, so she is unable to make the same transaction twice in the first place. Hence, only one of Amy or Bob’s blocks can be added — and this is determined by a consensus mechanism.
Consensus mechanisms
Proof-of-work: Miners are incentivized by a process called “proof of work” to help validate these transactions — they are given rewards, usually cryptocurrency e.g. Bitcoin, to verify the transactions. They must solve a complex mathematical problem (“mining”) to add the transaction to the blockchain and earn the reward. Simply put, mining is very difficult and requires a lot of computing power and energy. Miners will also compete with each other to solve the complex math problem — the one who solves it first will get their block added to the blockchain. Recall the earlier example of Amy and Bob — whoever solves this complex problem first will be able to add their block of validated transactions to the blockchain.
Miners often come together and concentrate their computers/computing power to solve the problems. When they solve the problems, they share the rewards given by the blockchain network. As the blockchain network grows bigger, the problems get more difficult and require more computing power to solve.
Proof-of-stake: “Proof of stake” is another method to validate new transactions and reach “consensus”. Participants who wish to validate transactions and add their blocks to the blockchain must own a stake in the blockchain (i.e. some of the crypto built on the blockchain) to have an opportunity to verify the transactions. Essentially, participants put up their crypto coins owned as collateral, by putting them into a wallet which then freezes the crypto placed inside (“staking”). So out of the “pool” of crypto coins staked, a coin will be randomly selected and the participant who owns that coin will get to add his block of validated transactions to the blockchain.
Of course, most blockchains which use PoS require a minimum number of coins for staking. The more cryptocurrency they have staked on the blockchain, the more transactions they can validate — so for example, if a participant owns 1% of the cryptocurrency coins available, they can theoretically only validate 1% of the blocks. Hence, the more you stake, the more likely your block of validated transactions can be added to the blockchain, and the more you can earn.
So once a new block has been validated and gets added onto the existing blockchain permanently via the consensus mechanism — the transaction is completed. When each node accepts a new block of data, it saves and stores it on top of of all the other blocks it already has stored.
But what is in a block?
Each block on the blockchain possesses (1) its own hash, (2) the hash of the previous block, and (3) a time stamp (of when it is added to the blockchain), and of course, (4) the data.
The data that is stored in a block depends on the use of the blockchain. For a cryptocurrency blockchain, a block would contain data about cryptocurrency transactions, e.g. the sender, the receiver and the amount of cryptocurrency.
The hash is essentially like a “fingerprint”, which identifies the block and its contents. Just like a fingerprint, it is always unique — different from any other hashes in any other blocks. A hash’s purpose is to prevent changes to the original data or block. If any data in the block is altered, the hash of the block will change (for example, “I pay Sam 1 Bitcoin” is changed to “I pay Sam 2 Bitcoins” or “I pay Sam 1 Bitcoin” is changed to “Sam pays me 1 Bitcoin”). And if the hash on a block changes, it is no longer the same block.
Having the hash of the previous block in a current block makes the blockchain secure. This is because a hacker who tampers with a particular block will change its hash. And in turn, all of the subsequent blocks will become invalid because they no longer store a valid hash of the previous blocks.
When tampering occurs and the hashes do not match, the tampered block and all subsequent blocks will no longer be chained to the (untampered) blocks before the tampered block. All users will know that a block has been altered and will reject this alteration by shifting back to a previous untampered record of the blockchain where all the blocks are still chained together.
In other words, if a hacker tries to amend any single block, all the subsequent blocks in the blockchain will also have to be amended as their hash also depends on the previous block,

Once a block is tampered with, its hash will change and all subsequent blocks will become invalid because the “previous hashes” are now different.
Conclusion
So that’s it for the basic introduction to blockchain. We now know what a blockchain is, and how data gets recorded and stored on a blockchain. We’ll explore more about the characteristics, benefits, shortcomings, and applications of blockchain in another article.
Now, isn’t it be less daunting when someone asks you, “hey, so tell me, how does this blockchain thing actually work?”
[1] IEEE Communications Surveys & Tutorials (2018) “Security Services Using Blockchains: A State of the Art Survey”
[2] PWC, “Making sense of bitcoin, cryptocurrency and blockchain”
[3] twilio (2018) “What is Public Key Cryptography?”
*To know more about the useful characteristics of blockchain and blockchain’s various applications, read more here.








